APWG Q2 Report: Phishers Combine Tactics and Resources in Newest Attack Schemes
CAMBRIDGE, Mass., August 26, 2024 (Newswire.com) - The APWG’s new Phishing Activity Trends Report reveals that phishers are pivoting to best take advantage against online users, mixing and matching the tactics and Internet resources they use to optimize their felonious campaigns and maximize their ill-gotten gains.
Matthew Harris, Senior Product Manager, Fraud at OpSec, explained that phishers are increasing targeting social media and SAAS services with traditional email lures because ”these sites do not require high security,” Harris noted. Instead, OpSec has noticed that phishers are targeting banks and their users differently. Banks require more elaborate security, such as two-factor authentication for online banking—usually codes sent the users’ mobile phones. Without those authentication codes, phishers can’t get into victims’ online financial accounts, and traditional email-based phishing doesn’t work
So instead of sending phishing emails to banking customers, fraudsters are increasingly calling potential victims directly, and luring them with text messages that may contain a phone number for the targeted subscriber to call. These phone-based methods are more immediate, and allow fraudsters to talk victims out of their sensitive information.
Researchers at APWG contributing member Fortra are also seeing phone methods being blended with email to carry out targeted attacks known as Business Email Compromise (BEC) attacks. These attacks can be especially costly: Fortra found that scammers requested an average of $89,520 per attempt in Q2 2024.
“The hybrid vishing attacks we track typically begin as an email indicating the recipient has been charged for a product or service,” said John Wilson, Senior Fellow, Threat Research at Fortra.
“The messages instruct the recipient to call a phone number if they wish to cancel their order and obtain a refund. In the second quarter of 2024, Norton/LifeLock was the most popular brand used as a lure in these attacks, mentioned in 39 percent of the hybrid vishing messages we encountered in Q2 2024,” Wilson said.
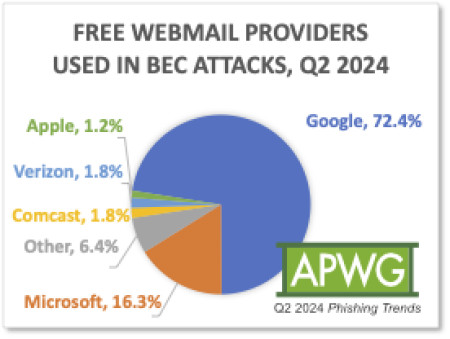
When fraudsters use email, they prefer to use free email services. Fortra found that 72 percent of Business Email Compromise (BEC) attacks in Q2 2024 were launched using a free webmail domain. The remaining 28 percent of BEC attacks utilized a combination of maliciously registered domains and compromised email accounts. Google’s Gmail was by far the most popular free webmail provider for BEC scammers, used for 72.4 percent of the free webmail accounts that scammers set up for BEC scams in Q2 2024.
The report also reveals that in Q2 2024, APWG observed 877,536 phishing attacks, decreasing from 963,994 attacks in the first quarter of 2024. APWG data curators suspect that the Q1 to Q2 decrease is due in part to a recent reporting issue: email providers have been making it more difficult for users to report phishing to APWG and to other anti-abuse organizations and law enforcement authorities.
Note on Phishing Report Curation and Archival Enterprises for Researchers
For years, APWG has asked users to forward suspected phishing emails to reportphishing@apwg.org for processing and analysis. Detailed complaints and subsequent testing made it clear some major email providers are now blocking these outbound messages forwarded by the original recipients. (Ironically, these providers deliver the phishing emails to their users, but then prevent their users from reporting out the phishing.)
The situation suggests the providers are not finding the phishing URLs in the emails they are delivering to their users, but are later finding the phishing URLs when the user tried to forward an email message, and are blocking those. To help get around this issue, APWG Engineering is setting up new web forms for users.
APWG is organizing new report-entry pages to be “mobile friendly” Web forms, letting users submit phish received via Text or SMS, as well as maintaining its reports page for email-based phish.
“Outbound email filtering is interrupting clearance of phish reports for cybercrime suppression that industry worldwide requires. By dint of that same scenario, law enforcement aren’t getting them either,” observed APWG VP of Operations Pat Cain.
The full text of the report is available here: https://docs.apwg.org/reports/apwg_trends_report_q2_2024.pdf
Media Contacts
For media inquiries related to the APWG, please contact APWG Secretary General Peter Cassidy (pcassidy@apwg.org, +1.617.669.1123). Or for company-specific content related to this release, please contact: Stefanie Wood Ellis of OpSec Security (sellis@opsecsecurityonline.com); Rachel Woodford of Fortra (Agari and PhishLabs) (Rachel.Woodford@fortra.com).
About the APWG
Founded in 2003, the Anti-Phishing Working Group (APWG) is the global industry, law enforcement, and government coalition focused on unifying the global response to electronic crime. Membership is open to qualified financial institutions, online retailers, ISPs and Telcos, the law enforcement community, solutions providers, multilateral treaty organizations, research centers, trade associations and government agencies. There are more than 2,200 companies, government agencies and NGOs participating in the APWG worldwide. APWG's apwg.org and stopthinkconnect.org websites offer the public, industry and government agencies practical information about phishing and electronically mediated fraud as well as pointers to pragmatic technical solutions that provide immediate protection. The APWG is co-founder and manager of the global STOP. THINK. CONNECT. campaign, most recently deployed as the national cybersecurity awareness campaign of Argentina, and founder/curator of the Symposium on Electronic Crime Research, the world's only peer-reviewed, published conference dedicated specifically to electronic crime studies (https://ecrimeresearch.org/ecrime-symposium/). APWG advises hemispheric and global trade groups and multilateral treaty organizations such as the European Commission, the G8 High Technology Crime Subgroup, Council of Europe's Convention on Cybercrime, United Nations Office of Drugs and Crime, Organization for Security and Cooperation in Europe, Europol EC3 and the Organization of American States. APWG is a member of the steering group of the Commonwealth Cybercrime Initiative at the Commonwealth of Nations. Among APWG's corporate sponsors are: AI Spera,Acronis, Adobe, AhnLab, AT&T, Arteria Communications, Allure Security, AREA 1, AIT, appgate, Apple, Asurion Insurance Services, Avast, Away AI, AXUR, BW CIRT, Bambenek Consulting, Banelco CSIRT, BanCERT, Bolster, Booz Allen Hamilton, BrandShield, Browlser, ByteDance, CHT Security, Canva, Central Bank of Jordan, Check Point, Cipherbit (Grupo Oesia), Cisco, CLARO, Cloudflare, Cloudmark, COFENSE, Coinbase, Comcast, CrowdStrike, CSC, CSIRT BANELCO, CSIS, Cyan Digital Security, Cyble, Cyren, Cyxtera, CZ.NIC, DS Lab, DigiCert, dmarcian, DNS Filter, DNS Belgium, EBRAND, Entrust Datacard, ESET, FirstRand, Fortinet, Fortra, FraudWatch, GetResponse, GMS Securidad, Group-IB, Guidewire, Hitachi Systems, .ID, ICANN, Identity Digital, Infoblox, Ingressum, INKY Technology Company, IQ Global, Kaspersky, KnowBe4, Lenos Software, LinkedIn, LINE, Looking Glass, LSEC, Material Security, McAfee, Meta, Mimecast, NCA, NAVER, Netcraft, NetSTAR, Nominet, Opera, OpSec Security, Palo Alto Networks, PANDI, PayPal, Proofpoint, Qintel, Rakuten, Recorded Future, Redsift, REDIRIS, ReversingLabs, RiskIQ, RSA, S2W Lab, SafeGuard Cyber, Salesforce, Secutec, Seven & i Holdings, Co. Ltd, SHRESHTA, SIDN, SlashNext, Sophos, Spamhaus Technology, SWITCH, Symantec, Telefonica, TEMU, Tessian, Thomsen Trampedach, ThreatSTOP, TNO, Tracer, TrendMicro, Trustwave, Twilio, Unbiased Security, Vade, Verisign, Viettel Cyber Security, WMC Global, Webroot, workday, ZeroFOX, ZibaSec, Zimperium, YARXIX, ZIX, .XYZ, and zvelo.
Source: APWG
